Overview
A critical Remote Code Execution (RCE) vulnerability has been discovered in the widely used Bit File Manager plugin for WordPress, affecting over 20,000 websites. This security flaw could allow attackers to remotely execute arbitrary code on vulnerable websites, leading to potential full site takeovers.
Given the severity of the vulnerability, it is strongly recommended that users of the Bit File Manager plugin update or deactivate the plugin immediately to mitigate any potential risks. Failure to address this issue promptly could expose websites to serious security threats, including data breaches, malware injections, and unauthorised access.
What Is Remote Code Execution (RCE)?
Remote Code Execution (RCE) is one of the most dangerous vulnerabilities a web application can face. In an RCE attack, a malicious actor can run arbitrary code on the server that hosts the vulnerable website, potentially gaining complete control over the system. The attacker could do the following:
- Install malware or backdoors
- Exfiltrate sensitive data, such as user credentials or personal information
- Modify or delete website files and content
- Use the compromised site for further attacks, including phishing and spreading malware
The vulnerability in the Bit File Manager plugin specifically allows an attacker to upload malicious files or execute scripts remotely due to a lack of proper validation and sanitisation in the file management functionality.
Affected Plugin: Bit File Manager
The Bit File Manager plugin enables WordPress users to manage their site’s files directly from the WordPress dashboard, including uploading, editing, and deleting files. Unfortunately, due to a flaw in the way it handles user input, particularly in the file upload functionality, attackers can exploit the plugin to upload malicious files that are then executed on the server.
The vulnerability affects all versions of Bit File Manager up to the latest release at the time of discovery.
Impact and Potential Risks
This vulnerability poses a severe risk for WordPress websites using the Bit File Manager plugin. If exploited, attackers can potentially:
- Gain full control over the website
- Steal sensitive user information, including login credentials, personal data, and financial information
- Inject malicious code into the site, turning it into a platform for distributing malware
- Deface the website or delete important files
- Use the compromised site for further attacks on other websites or systems
Given the plugin’s user base, it is estimated that over 20,000 WordPress sites are vulnerable, making it a widespread and critical issue.
Mitigation and Recommendations
It is urgent for site administrators using the Bit File Manager plugin to take immediate action to protect their websites. The following steps should be followed:
- Disable or remove the Bit File Manager plugin from your site until a patch is released here’s how to do it:
- Check for plugin updates regularly. If the plugin’s developers release a security patch, update the plugin to the latest version as soon as possible.
- Check your site for signs of compromise. This can include unfamiliar files in your file manager, unexpected behavior on your website, or warnings from security plugins.
- Implement additional security measures, such as:
- Installing a WordPress security plugin like Wordfence or Sucuri, which can help detect and block malicious activity.
- Using firewall protection to block suspicious IP addresses and traffic.
- Regularly auditing user roles and access permissions.
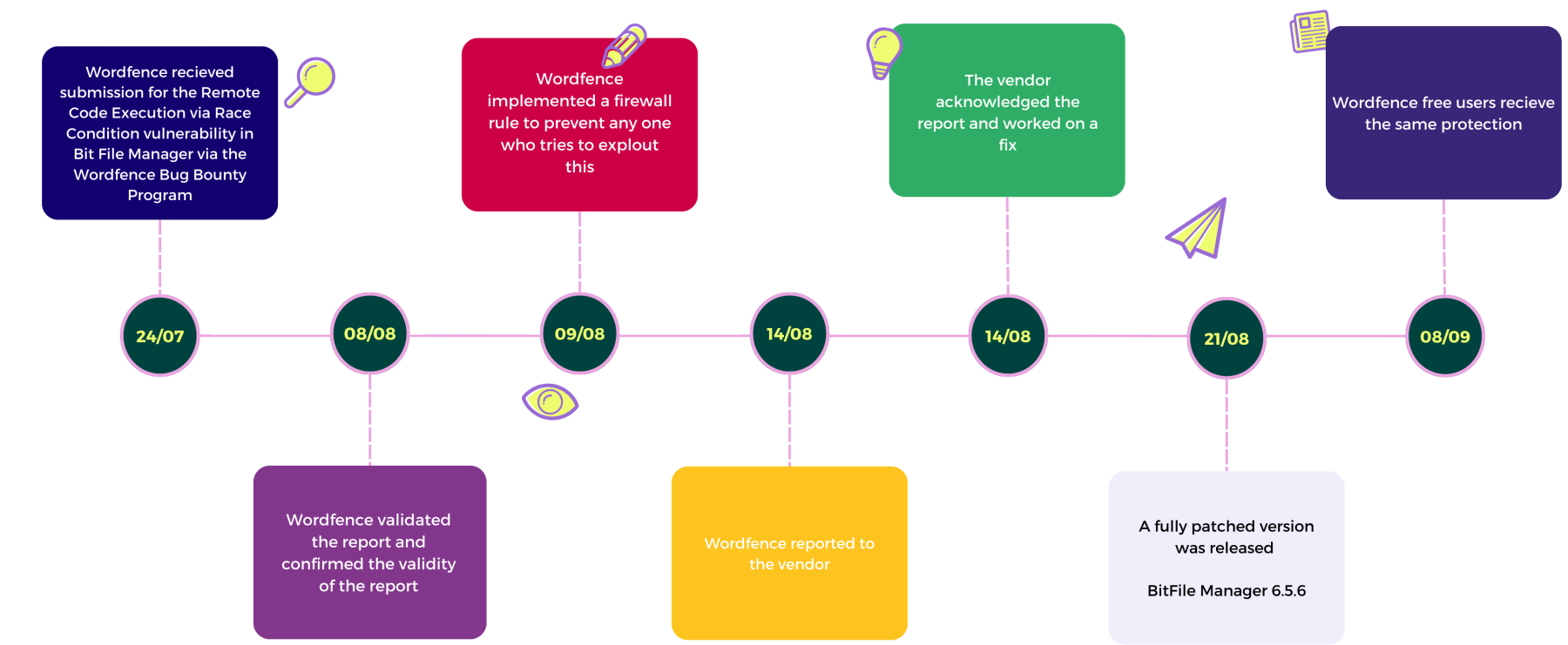
The WordFence Timeline
Preventive Measures
To protect your WordPress website from similar vulnerabilities in the future, consider the following best practices:
- Regularly update all plugins, themes, and WordPress core files. Vulnerabilities are often discovered and patched in subsequent updates.
- Implement privilege access by ensuring that only authorised users have access to sensitive site functionality like file management.
- Use two-factor authentication (2FA) for logging in to the WordPress admin area.
- Consider using manual file management through secure FTP instead of relying on file management plugins with web-based access.
Conclusion
The discovery of a critical Remote Code Execution vulnerability in the Bit File Manager plugin highlights the importance of website security, especially for plugins that provide access to file management functionalities. This flaw could allow attackers to gain full control over WordPress websites, placing them at significant risk.
If you are using the Bit File Manager plugin, it is crucial that if you havent updated the plugin you must deactivate or remove the plugin immediately and monitor for updates from the developers. Additionally, taking proactive security measures can help prevent future attacks and ensure the safety of your website and data.
For more information on WordPress security and steps to protect your site, feel free to reach out on our contact page or feel free to book a discovery call


